A security audit establishes a set of criteria that organizations check against to ensure that they are meeting internal security policies and complying with external regulations. Security audit helps an organization assess how secure its network and systems are against potential cyberattacks.
How Does a Security Audit Work?
A security audit works by testing whether an organization’s information system is adhering to a set of internal or external criteria regulating data security. A security audit compares the organization’s actual IT practices with the standards that are relevant to it and identifies areas for remediation and growth.
Internal audits include the company’s IT policies and procedures and security controls. External audits include federal regulations like the Health Insurance Portability and Accountability Act (HIPAA) and standards set by National Institute for Standards in Technology (NIST), etc.
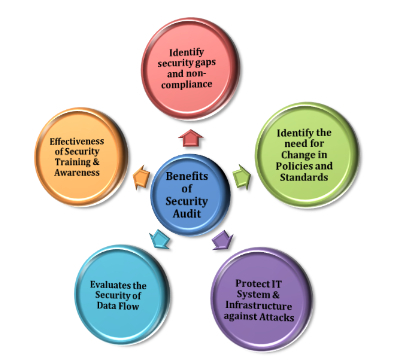
Benefits of Security Auditing
4 Types of Security Audit Every Business Should Conduct
Below are some of the main types of audits that businesses can use to improve their security posture. It is important to remember that no two businesses are alike, and therefore no single report will be right for every business. The key is to choose the type of process that best suits your company needs and budget.
- Risk Assessment- Risk assessment identifies, evaluates, and prioritizes potential vulnerabilities to various information assets (i.e., systems, hardware, applications, and data) and then prioritizes the various risks that could affect those vulnerabilities.
- Vulnerability Assessment- Vulnerability Assessment is the most performed security test. It is automated testing and done within a limited scope to track down the security bug or flaws present within the assets. Assets could be application, network, infrastructure, data, etc., depending upon the assessment objective.
- Penetration Test- Penetration Testing involves the exploitation of categorized security flaws found in the vulnerability assessment. It is performed as a proactive approach to identify security gaps and often to meet compliances and regulations.
- Compliance Audit- Companies that violate laws and regulatory standards are subject to a variety of punishments, including fines against the company and reputation damage with customers. Enterprise systems that process information are guided by security compliance frameworks like National Institute of Standards and Technology (NIST), Health Insurance Portability and Accountability Act (HIPAA). Such frameworks outline compliance audits as a statutory requirement, which help reduce the company’s legal risk.
Cybersecurity Auditing
The modern Cybersecurity landscape continues to evolve, with newer security threats emerging frequently and regulatory requirements changing to address them. As a result, tackling consistent threats is often considered one of the most effort-intensive tasks of an organization.
A Cybersecurity audit provides a comprehensive assessment of information systems to evaluate compliance and identify gaps in security policy implementation. The auditing process involves closely examining the firm’s digital assets and security controls to ensure they satisfy compliance standards requirements.
Best Practices for Cybersecurity Audit
Cybersecurity audit is an important procedure that evaluates and validates an organization’s security policies and processes. Below are some of the best practices that can be followed for cybersecurity audit:
- Define the Scope of the Audit- It is very important that the scope and extent of audit is defined so as to determine the time, workforce and the budget that will be required to complete the audit. Identify the specific goals that organization is aiming to achieve through the audit process.
- Review the compliance standards-The more your controls, procedures and systems gel, the lower is your risk. Most organizations have one or more compliance standards that they strive to meet, such as HIPAA, SOC, etc.
- Review and Update Internal Policies-Check for systematic flaws in internal policies and remove any issues you identify, assess whether there is an opportunity for improvement, and add additional policies if necessary.
- Make IT Risk Assessments a Continuous Process –Identifying and mitigating risks needs to be a continuous process to ensure that your organization is prepared to address new threats as they arise.The recommended best practice is to re-evaluate your risks at least every one to three years.
- Use cloud services for storing evidence -Utilize cloud storage services to collect audit evidence. The cloud services enable gathering adequate, appropriate audit evidence remotely. Ensure all security controls are implemented in the cloud service being used for restricting any data leakages.
- Get all the Team Members On Board-When equipped with the right training and support, employees are a valuable asset for protecting sensitive data. While the type and detail of training may vary depending on the risk level of their roles, every staff member with access to IT assets needs some form of security awareness training. The organization also needs processes and procedures that dictate the best practices that staff must follow.
Dinoct and Security Audit
Dinoct conducts internal audits on a quarterly basis. During the process, we review the company’s security systems, policies, and procedures. Internal Audits are performed to ensure compliance with regulatory requirements and also check the effectiveness of the company’s security measures and identify any gaps that can be filled.
Dinoct also conducts 3rd party audits as per business need.
Final Thoughts
The cyber threats landscape is evolving every day with the advancement of attack vectors. It has become crucial to perform an appropriate security assessment to identify and close the open path with robust measurements. Conducting regular audits can help identify weak spots and vulnerabilities in your IT infrastructure, verify your security controls, ensure regulatory compliance, and more. Periodical audits can help increase the security of your data while improving your reputation with customers and business partners.






